When new security threats are discovered and referenced on the internet, malicious users receive this info as well. Affected IT environments are easy targets. This is were Vulnerability Assement comes to play. Discover how it can reduce this risk and increase your global IT visibility!
What is MITRE and CVE?
As we just mentioned, each security threat is referenced on a dictionary maintained by the MITRE*. This is a non-profit company, dedicated to solving problems for a safer world.
They manage a big database that contains all the information about every discovered threat. The identification numbers the use are named CVE (Common Vulnerabilities and Exposure) and those used to define the discovered vulnerabilities.
Each CVE contains a small description of the vulnerability, some references, the impacted product, the date of the detection and its severity.
A Vulnerability Assessment tool will use all this information to perform his job.
What can a Vulnerability Assessment Tool do for you?
Now that the basics are set, we are good to go and dive a little deeper into what this tool can provide to you and your company.
- Some customers require prove or a stamp that your company is frequently checking its IT infrastructure's security and takes action to re-mediate the potential security flaws.
- Your management wants to have a global overview of your IT infrastructure's security.
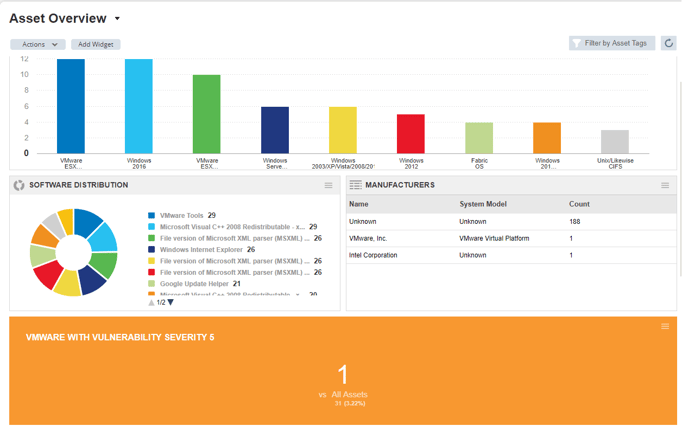
- You, as an IT technical guy, want to have a complete view of the assets on your network and concrete solutions to solve your security risks.
- The IT team has difficulties to prioritize your actions and/or doesn't have enough time to deal with all the security issues.
- ...
For all of these reasons and many others, it is time to look deeper into a Vulnerability Assessment tool which will provide all these advantages and much more.
What's the EASI point of view?
At EASI, we have chosen to trust Qualys on this topic. In partnership with them since multiple years and based on our experience we are able to help you for the complete process.
- Defining the scope
- Report presentation
- Scanning configuration
- Interpretation of the results
- ...
You name it, our Security Engineers are here to support you at any way you would like. So if you want to talk or if you would like some more information. Don't hesitate to contact us.






