Phishing attacks remain very popular with cybercriminals, especially since the beginning of the pandemic. Since then, the number of attacks targeting companies has strongly risen.
Hackers are very resourceful and will not back down from anything to try and steal your private or companies’ data and ultimately launch a ransomware attack.
The problem is that not many people know how easy it is to fall for it. Even to the trained eyes. There exists a pernicious type of phishing attack that uses a simple tool called Evilginx. The level of simplicity and damage it can do to private individuals and companies really gave me the chills.
With this article, I want to raise awareness and give you some pointers to protect yourself.
What is Evilginx?
Put simply, Evilginx is a man-in-the-middle framework that allows a hacker to steal credentials and authentication tokens, ultimately allowing them to bypass any form of 2 factor-authentication (2FA).
What’s the difference with “basic” phishing attacks?
There is one major difference between attacks using Evilginx and the ones that do not.
With basic phishing attacks, hackers try to recreate, as faithfully as possible, lookalike HTML templates of sign-in pages (from Outlook, LinkedIn, etc). They will then attempt to lure the victims into entering their credentials, which are then logged and stolen by the hacker.
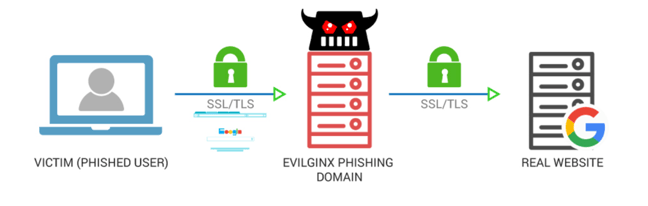
Evilginx takes it one steps further. Instead of showing templates of lookalike pages, it acts as a relay between the real website and the phished user. After clicking on a malicious link, phished victims are sent to the real website, unaware that Evilginx is capturing the data being transmitted between the two parties.
Not even 2-factor authentication can save you
Today, 2FA remains one of the best ways to prevent basic phishing attacks. If a hacker manages to retrieve your login and password, he won’t be able to access your account because 2FA acts as a second line of defense.
This is a whole different ball game with Evilginx. Even if a phished user has 2FA enabled, the attacker will still be able to remotely take over the account. How? Like I said before, Evilginx acts as a man-in-the-middle between the actual target website and the victim to intercept credentials and authentication tokens.
When the victim enters its credentials and is asked to provide a 2FA challenge answer, he will receive a code because he is talking to the real website, with Evilginx sitting in the middle.
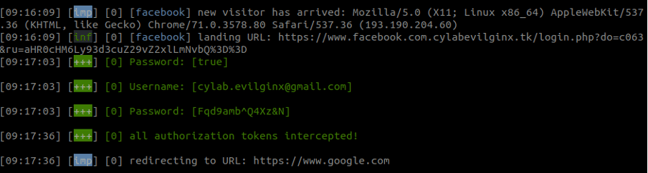
I don’t want to get too technical about what happens in the background. What you need to know is that after a 2FA challenge is completed and the website confirms its validity, a session token is generated in form of a cookie. This cookie is intercepted by Evilginx and saved, allowing the attacker to bypass 2FA protection.
At this point, the hacker now holds all the key to successfully connect to the victim’s account, fully bypassing 2FA protection.
If you want to see Evilginx in action, I have created a short demonstration video:
3 ways to protect yourself from Evilginx attacks
Like any phishing attempts, there are simple ways to protect yourself from it.
1.Double check the website domain
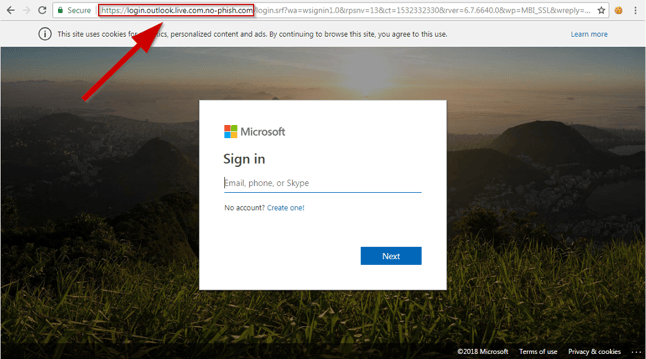
One of the (only) flaw of Evilginx, is that hackers need to register their own domain. Which will be (slightly) different than the actual domain of the website.
For example, if a hacker is targeting Outlook, they will probably register a domain name such as outloook.com or outl00k.com, making it difficult for potential victims to spot a difference.
To make sure you are not falling for an Evilginx attack, always check the legitimacy of the website domain in the address bar.
2.Invest in security awareness
Evilginx represents a real danger for companies because it only takes one employee to get phished and allow attackers to steal a vast amount of (confidential) data.
That is why end users are often considered to be the weakest links of a company’s security posture. Providing employees with proper trainings and educate them to raise awareness, is the best way to prevent any security breach in a company.
3. Use Universal 2nd factor Authentication
Universal 2nd factor Authentication is a physical hardware key (a bit like a USB stick) that talks directly with the website. If the domain written in the address bar of the browser does not match the domain expected used for the connection, the communication will be interrupted.
Universal 2nd factor authentication guarantees you that you will never get phished, even with Evilginx.